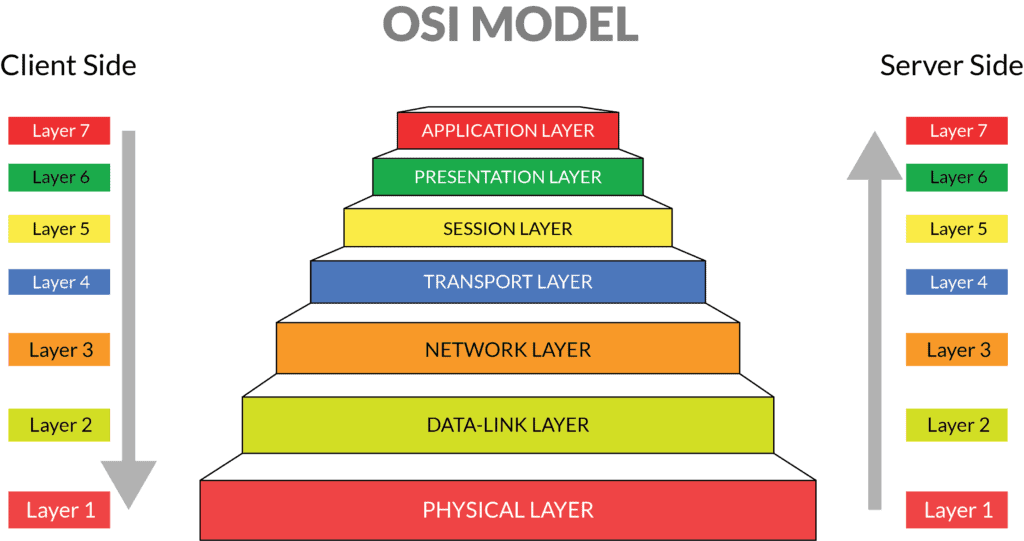
OSI stands for Open System Interconnection (Internet protocol suite) is a reference model and it conjointly web protocol suite that describes seven layers that laptop systems use to speak over a network. it had been the primary normal model for network communications, adopted by all major laptop and telecommunication corporations within the early Nineteen Eighties.
The fashionable web isn’t supported OSI, however on the less complicated TCP/IP model. However, the OSI 7-layer model remains wide used, because it helps visualize and communicate however networks operate, and helps isolate and troubleshoot networking issues.
OSI was introduced in 1983 by representatives of the foremost laptop and medium corporations, and was adopted by ISO as a global normal in 1984. source
OSI Model Layers:
| No | Layer | Function | Unit | Protocols/Services | Devices |
| 7 | Application | network application services and processes | data | FTP, TFTP, HTTP, SMTP, SMB, NCP, Telnet, NTP, File & Print, DNS | gateway |
| 6 | Presentation | encryption, formatting, compression, translation | data | ASCII, JPEG, GIF, TIFF, MIDI, MPEG, MIME, Quicktime | gateway |
| 5 | Session | establishes maintains, manages network connections and sessions | data | RPC, ZIP, SCP, SQL, NetBIOS, NFS, ASP, LDAP, SSL, SMB | gateway |
| 4 | Transport | end-end error recovery, connectivity, flow control | segments | TCP, SPX, UDP, NBP, NCP. NetBEUI, SCTP | gateway |
| 3 | Network | routing, forwarding of packets; sequencing of datagram | packets | IP, IPX, ARP, RARP, DHCP, BootP, ICMP, RIP, BGP, OSPF, IPSec | router, brouter |
| 2 | Data Link | encoding/decoding of packets into bits; frame synchronization, error checking | frames | MAC, LLC, PPP, ATM, frame relay, 802.11b/g, L2TP, FDDI | switch, bridge |
| 1 | Physical | electrical, mechanical, lightwave, radio frequency, media specifications | bits | Ethernet, WiFi, Token Ring, BRI, RS232, V.35 | hub, NIC, WAP |
TCP/IP Model Layers:
The OSI Model we simply checked out is simply a reference/logical model. it internet protocol suite had been designed to explain the functions of the communication system by dividing the communication procedure into smaller and less complicated parts. however once we name the TCP/IP model, it had been designed and developed by Department of Defense (DoD) in Sixties and is predicated on normal protocols. It internet protocol suite stands for Transmission management Protocol/Internet Protocol or TCP science web Protocol Suite . The TCP/IP model is a elliptical version of the OSI model. It contains four layers, in contrast to seven layers within the OSI model. The layers are:
- Network Access/Link Layer
- Internet Layer
- Host-to-Host/Transport Layer
- Process/Application Layer
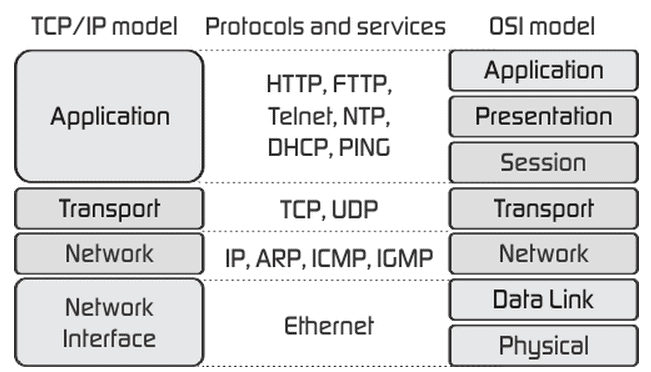
TCP science web Protocol Suite
| TIC/UDP port | Protocol | Full Name | Description | OSI Layer |
| 7 | ICMP | Internet management Massage protocol | Used for error (echo)reporting,flow management and route testing | Network |
| 20/21 | FTP | File transfer protocol | Protocol for uploading and down-loading files to and from a far off host; conjointly accommodates basic file management tasks | Application |
| 22 | SSH | Secure Shell | Like Telnet permits sessions to be opened on a far off host, however provides authentication and encoding capabilities | Application |
| 22 (work with SSH) | SFTP | Secure file Transfer Protocol | Protocol that performs the same operate to FTP, however Provides safer authentication and encoding mechanisms | Application |
| 22 (work with SSH) | SCP | Secure Copy Protocol | Protocol that uses Secure shell (SSH) Technology to supply a secure thanks to copy files between systems | Application |
| 22 (work with SSH) | LDAP | Lightweight Directory Access Protocol | Provides a mechanism to access directory Services systems | Application |
| 23 | Telnet | Telnet | permits Sessions to be opened on a far off host | Application |
| 25 | SMTP | Simple Mail Transfer Protocol | Delivers emails between email servers; causation of emails; uses TCP | Application |
| 465 | SMTPs | Secure straightforward Mail Transfer Protocol | Delivers emails between email servers; causation of emails; uses TCP | Application |
| 53 | DNS | Domain Name System | Translates hostnames to science addresses; uses TCP (zone transfers), UDP (queries | Application |
| 69 | TFTP | Trivial file Transfer protocol | Mechanism for transporting email across networks | Application |
| 80 | HTTP | Hypertext Transfer protocol | Protocol for retrieving files from an internet server. | Application |
| 109 | POP2 | Post workplace Protocol – Version 2 | Used for retrieving email from a server on that the mail is stored | Application |
| 110/143 | POP3/IMAP4 | Post workplace Protocol version 3/ web Message Access Protocol Version 4 | Used for retrieving email from a server on that the mail is stored | Application |
| 995/993 | POP3s/IMAP4s | Post workplace Protocol version 3/ web Message Access Protocol Version 4 | Used for retrieving email from a server on that the mail is stored | Application |
| 119 | NNTP | Network News transport Protocol | Protocol used for accessing and downloading messages from Internet-based newsgroups. | Application |
| 123 | NTP | Network Time Protocol | Used to communication time synchronization data between devices | Application |
| 443 | HTTPS | Hypertext Transfer protocol Secure | Secure Protocol for retrieving files from an internet server. | Application |
| 515 | LPR | Line printer remote | Provides a mechanism to send printing tasks to a print server | Application |
| IP | Internet Protocol | Connectionless protocol used for moving knowledge around a network. | Network | |
| TCP | Transmission management Protocol | Connection-oriented protocol that provides flow management, sequencing, and retransmission of born packets | Transport | |
| UDP | User datagram protocol | Connectionless various to TCP that’s used for application that don’t need the functions offered by TCP | Application | |
| ARP | Address Resolution Protocol | Resolves science addresses to mack addresses, to alter communication between devices | Network | |
| RARP | Reverse Address Resolution Protocol | Resolves mack addresses to science addresses | Network | |
| IGMP | Internet cluster Management protocol | Protocol used for communication between devices associate degree exceedingly|in a very} multicast group | Network | |
| ICS | Internet association Sharing | Connects multiple laptops on an area network to the net through one association ANd science address; uses NAT | Network | |
| WINS | Windows web Naming Service | Resolves a number NetBIOS name or computer name into an science address; utilized in bequest Windows | Application | |
| Zeroconf | Zero Configuration | Connects networking devices exploitation an LAN cable; no configuration or DHCP required | Application | |
| SMB | Server Message Block | Shares files, directories, ANd services; message format utilized by DOS; permits UNIX system/Linux and Windows machines to share files | Application | |
| Samba | – | Provides file and print services to SMB clients; runs on UNIX system and Linux | Application | |
| ICA | Independent Computing Architecture | The core of Citrix presentation server that allows Windows or UNIX server to run an application for multiple users simultaneously | ||
| Apache | – | A standard property right UNIX-based net server | Application | |
| AFP | Appletalk File Protocol | A file sharing protocol used with TCP/IP to allow non-apple computers to access apple servers |
Remote access protocols and services
| Name | Meaning | Function |
| RAS | Remote Access Service | Used for client remote access to a network |
| PPP | Point-Point Protocol | Used to establish an internet connection between serial point-to-point links; provides for dial-up connnections to networks |
| SLIP | Serial Line Internet Protocol | Used to connect to the internet via a dial-up modem; older, slower, less reliable than PPP |
| PPPoE | PPP over Ethernet | Uses PPP over Ethernet to connect an ethernet LAN user to the internet using an ADSL or cable modem; users share a broadband connection |
| PPTP | Point-Point Tunnel Protocol | A form of encryption that provides a tunnel for secure connections over the internet; used to create VPN |
| VPN | Virtual Private Network | A private, secure, point to point connection from a company LAN to the remote users and wireless nodes using the internet |
| RDP | Remote Desktop Protocol | connects a client to a network via a terminal server and uses authentication to establish connection to run applications and printers remotely |
Security protocols

| Name | Meaning | Function |
| IPSec | Internet Protocol Security | Provides authentication and encryption over the internet; works with IPv4 and IPv6; used to secure VPN |
| L2TP | Layer 2 Tunneling Protocol | Supports non-TCP/IP protocols VPN over the internet; combines the best features of PPTP and L2F |
| SSL | Secure Sockets Layer | Uses a private key to encrypt data that is transferred over the SSL connection; service independent and can secure different network applications |
| WEP | Wired Equivalent Privacy | Encrypts and protects data packets over radio frequencies; does not offer end-end security |
| WPA | WiFi Protected Access | Offers improved data encryption and user authentication using the wireless devices MAC address; uses TKIP encryption |
| AES | Advanced Encryption Standard | A cryptographic cipher that uses Rijndael algorithm |
| PGP | Pretty Good Privacy | An encryption utility based on public key encryption designed to encrypt email transmissions |
| 802.1x | – | Method for passing EAP over both wired and wireless networks; provides authentication services for wireless networks not using PPP |
Authentication protocols
| Name | Function | |
| CHAP | Challenge Handshake Authentication Protocol | Uses a hashed algorithm MD5 that provides client response encryption; weak and one-way authentication protocol |
| MS-CHAP | Microsoft Challenge Handshake Authentication Protocol | Has two versions used in Windows systems that offers more security; version1 not compatible with version2 |
| PAP | Password Authentication Protocol | The weakest authentication protocol that sends username and password in clear text over the network to be verified by RAS |
| RADIUS | Remote Authentication Dial-in User Service | An industry standard that provides authentication, authorization, and accounting services |
| Kerberos | – | A fully-fledge security system that uses secret key cryptography |
| EAP | Extensible Authentication Protocol | A general protocol often used by a wireless devices to connect to a RADIUS server; TLS uses certificates such as smart cards |
Routing protocols
| Name | Meaning | Function |
| RIP | Routing Information Protocol | Finds the quickest route between two computers; offers a maximum of 16 hops between routers before deciding that a packet is undeliverable |
| OSPF | Open Shortest Path First | A descendant of RIP that increases its speed and reliability; much used on the internet; accepts 256 hops between routers |
| IGRP | Interior Gateway Routing Protocol | A propriety protocol from Cisco that takes bandwidth, latency, reliability, and current traffic load into consideration |
| EGP | Exterior Gateway Protocol | A distance vector protocol that uses polling to retrieve routing information |
| BGP | Border Gateway Protocol | Used to span autonomous systems in the internet; used at the edge of networks; designed to supersede EGP |
| NLSP | Netware Link Services Protocol | A link state routing protocol that was designed to reduce wasted bandwidth associated with RIP |
| RTMP | Routing Table Maintenance Protocol | Used by Appletalk to ensure that all routers in the network have consistent routing information |
You don’t get over an addiction by stopping using. You recover by creating a new life where it is easier to not use. If you don’t create a new life, then all the factors that brought you to your addiction will catch up with you again. — Unknown
I’m not sure exactly why but this site is loading very slow for me.
Is anyone else having this problem or is it a issue on my end?
I’ll check back later on and see if the problem still exists.
Here is my blog; comfort
Excellent goods from you, man. I’ve understand your stuff previous to and you are just too great. I actually like what you’ve acquired here, really like what you are stating and the way in which you say it. You make it enjoyable and you still care for to keep it sensible. I can’t wait to read far more from you. This is actually a wonderful website.
Remeber the crossroads, the highway, the tracks, a single light post, the giant window of our prison to the stars.