TCP/IP Network Protocols Suits
| Layer | Protocols/Services |
| Application | FTP, TFTP, HTTP, SMTP, SMB, NCP, Telnet, NTP, File & Print, DNS |
| Presentation | ASCII, JPEG, GIF, TIFF, MIDI, MPEG, MIME, Quicktime |
| Session | RPC, ZIP, SCP, SQL, NetBIOS, NFS, ASP, LDAP, SSL, SMB |
| Transport | TCP, SPX, UDP, NBP, NCP. NetBEUI, SCTP |
| Network | IP, IPX, ARP, RARP, DHCP, BootP, ICMP, RIP, BGP, OSPF, IPSec |
| Data Link | MAC, LLC, PPP, ATM, frame relay, 802.11b/g, L2TP, FDDI |
| Physical | Ethernet, WiFi, Token Ring, BRI, |
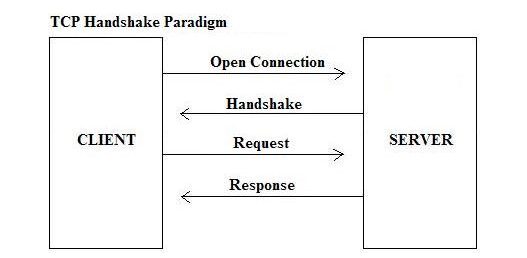
Transmission Control Protocol (TCP)
TCP network protocols functions at the transport layer of the OSL model and could be a connection-oriented protocol. TCP network protocols uses science as its network protocol. it’s answerable for breaking the information into manageable packets and making certain that the packets reach their destination. Whth connection-orionted protocols, a session is established through introductions . connection-oriented protocols can monitor that session to confirm that the packets have reached their destination. TCP network p etrotocols Provides reliabitity to science communication. Specifically, {tcp|transmission management protocol|TCP|protocol|communications protocol} adds options like flow control, sequencing, and error delection and correction. for this reson, higher-levell application that require secure delivery use TCP instead of it’s light-weight and connectionless brother, the user Datagram Protocol.
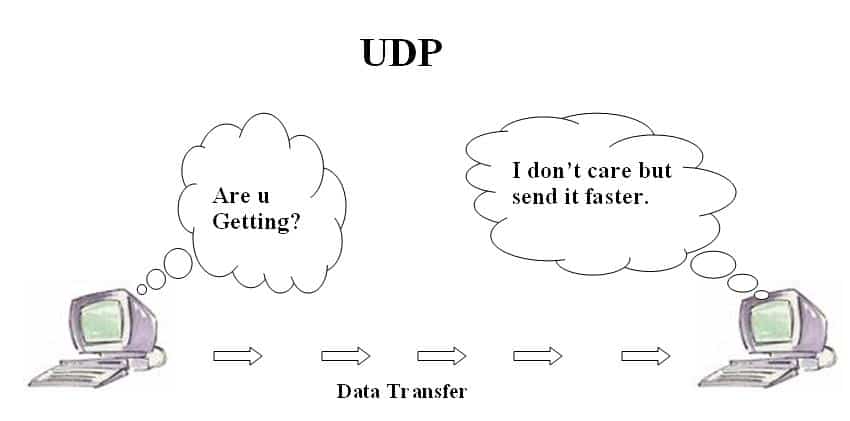
User Datagram Protocol (UDP)
UDP network protocols is that the protocol of transport layer of the OSI model and performs perform just like that of TCP however UDP network protocols could be a connectionless protocol and doesn’t guarantee information delivery.Both TCP and UDP use science as it’s transport protocol.
Because UDP doesn’t have to be compelled to guarantee information delivery it’s far more economical that TCP as while worries. for this reason application that don;t want the additional options of TCP, use UDP as their most well-liked protocol. UDP is additionally price effective in terms of information measure and process effort. a decent example of UDP network protocols is an internet station that sends information however doesn’t need to induce the confirmation information from the receiver aspect.
File Transfer protocol (FTP)
As the name suggests a FTP network protocols is employed for transferring file. The FTP is Associate in Nursing application layer protocol that has a way for uploading and downloading files from a foreign systems running FTP server software package. FTP uses the TCP transport protocol to ensure the delivery of information packets.
FTP network protocols has some basic security capabilities, like a capability to manifest users. However, instead of produce a user account for each user, you’ll piece FTP server software package to just accept anonymous logons. once you try this, the username is anonymous, and also the watchword is generally the user;s email address. Most FTP servers that provide files to the overall public operate during this means. FTP is fashionable for distributing files over the web however is additionally used at intervals organizations that realize it impractical to use regular email.
Secure File Transfer Protocol (SFTP)
We have already learned that FTP will manifest a user by checking the username and watchword. however FTP transmits information between sender Associate in Nursingd recover in an unencrypted format. this is often large security threat. the answer of this drawback is that the Secure file Transfer Protocol, that is predicated on Secure Shell (SSH) technology. SSH provides sturdy authentication between sender and reciver, additionally to cryptography capabilities.
Trivial File Transfer protocol (TFTP)
The Trivial file transfer protocol (TFTP) is that the minimal version of FTP. TFTP network protocols has no directory browsing skills like FTP; it will do noting however send and receive files. It will send a lot of smaller blocks of information than FTP, and there’s no authentication like FTP, thus it’s insecure. Few sites support it owing to the inherent security risks. FTP and TFTP square measure each application layer protocols; but, TFTP uses solely UDP as a transport protocol, creating it a connectionless protocol. As such, it’s a lower overhead than FTP.
The biggest distinction between TFTP and FTP is That TFTP could be a connectionkess protocol, exploitation solely the UDP transport protocol. Another feature that TFTP doesn’t provide is directory navigation. In FTP, commands will be dead to navigate around and manage the file system; TFTP offers no such capability. meaning TFTP needs a hard and fast location to transmit information.
In short….. Trivial File transfer Protocol could be a straightforward lockstep file transfer protocol that permits aclient to induce a file from or place afile into remote host. one in every of it’s primary uses is within the early stages of nodes booting from space|a neighborhood} area network. TFTP has been used for this application as a result of it’s terribly silple to implement.
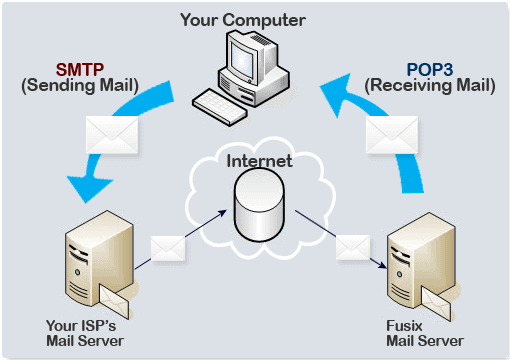
Simple Mail Transfer Protocol (SMTP) (Mailing Protocol)
Simple mail transfer protocol, a protocol for causing e-mail messages between severs. Most e-mail systems that send mail over the web use SMTP to send massages from one server to a different.
Post Office protocol virsion 3 (POP3) (Mailing protocol)
Post office protocol version three network protocols could be a customary mail protocol wont to receive emails from a foreign sever to a neighborhood email consumer. POP3 permits you to transfer email messages on your native laptop and browse them even once you square measure offline.
Internet Massage Access protocol (IMAP) (Mailing Protocol)
The Internet Massage Access protocol could be a customary mail protocol used fro accessing email on a foreign internet server from an area shopper. IMAP and POP3 area unit 2 most ordinarily used web mail protocol for receiving emails . each protocol area unit supported by all fashionable email purchasers and internet servers.
Difference Between IMAP and POP3
The POP3 protocol assumes that there’s only 1 shopper connected to the mailbox. In distinction, The IMAP Protocol permits concurrent access bymultiple shopper. IMAP is appropriate for if your mailbox is on the point of be managed by multiple users.
Hypertext transfer protocol (HTTP)
The Hypertext transfer protocol is an application protocol for distributed, collaborative and hypermedia information systems. HTTP network protocols is the foundation of ata communication for the world wide web. Hypertext is structured text that uses logical links (Hyperlinks) between nodes containing Text.
Hyper Text transfer protocol secure (HTTPS)
Hyper Text transfer protocol secure is that the secure version of hypertext transfer protocol, the protocol over that information is distributed between your browser and also the web site that area unit connected to. The ‘S’ at the tip of HTTPS stands for ‘Secure’. It means that all communication between your browser and also the web site area unit encrypted.
Secure Sockets Later (SSL)
SSL (Secure Sockets Layer) is a customary security protocol for establishing encrypted links between an online server and a browser in a web communication. The usage of SSL technology ensures that each one information transmitted between the net sever and browser remains encrypted. it’s use to hypertext transfer protocol.
Telnet
Telnet network protocols is the terminal emulation protocol. The function of Telnet is to allow the establishment of sessions on a remote host. A user can then execute commands on that remote host as if he were physically sitting at the system. Telnet is widely used to access UNIX and Linux systems, as well as to administer some managed networking equipment such as switches or routers. Telnet uses TCP as a transport layer protocol and functions at the application layer of the OSI model.
Secure Shell (SSH)
Secure shell is secure alternative to telnet. It is a program used to create a shell , or session. With a remote systems. SSH provides security by encrypting data as it travels between systems. It also provides more robust authentication systems that Telnet. Although SSH, like Telnet, is primarily associated with UNIX and Linux and systems, implementations of SSH are available for all commonly used computering platforms including windows and Macintosh. As discussed, SSH is the foundational technology for the secure File Transfer Protocol(SFTP).
Secure Copy Protocol (SCP)
Secure Copy protocol operates at the application layer of the OSI model. it is another protocol based on secure shell technology. SCP provides a secure means to copy file between systems on a networks. By using SSH technology, it encrypts data as it travels across the network, thereby securing it from eavesdropping. it is intended as a more secure substitute for the Remote copy protocol (RCP) SCP is most commonly associated with UNIX or Linux platforms, though it is available as a command line utility or as part application software for most commonly used computing platforms.
Internet Control Massage protocol (ICMP)
ICMP network protocols is not so famous like IP but it work with IP provide Error checking and reporting functionality many important network programs such as ICMP, ping, Traceroute (Tracert) rely on ICMP, IT is responsible for handling errors related to IP packets that cannot be delivered.
for example, if a packet cannot be delivered, a message called Destination Unreachable is sent back to the sending device so it will know that there was so undelivered message. Another important error message is “destination Unreachable” message . This error message has several sub types of messages that can be sent back to the host to find the problem.Network unreachable and and port unreachable are to destination unreachable massage that may be returned to help the host to determine the nature of the problem.
Well-known ping utility also uses the ICMP. ICMP is responsible for returning the error, IN addition to announcing errors, ICMP also announces network congestion for returning the error. In addition to announcing errors, ICMP also announces network congestion and timeouts field on a packet reaches zero. ICMP com be used for a number of functions. Ping sends a stream of ICMP echo requests to a remote host. if the host is able to respond, it does so by sending echo reply messages back to sending host. In that one simple process, ICMP enables the verification of the protocol suite configuration of both the sending and receiving nodes and any intermediate networking devices.
Internet Group Management Protocol (IGMP)
The Internet Group Management protocol is a communication protocol associated with the process of multi casting. Multi casing is a mechanism by which groups of network devices can send and receive data between the member of the group at one time, rather then separately sending messages to each device in the group.
IGMP network protocols is used by IP host and adjacent multicast routers to establish multicast group memberships. it is an integral part of the IP multicast specification, operating above the network layer, though it doesn’t Actually act as a transport protocol. IT is analogous to ICMP for unicast connections. IGMP can be used for online streaming video and gaming, and allow more efficient use of resources when supporting these uses. IGMP does allow some attacks, and firewalls commonly allow the user to disable it if not needed.
Line Printer Remote (LPR)
The Line printer Remote protocol is used to connect and maintain print server on a network. it is a generic printing protocol supported bt all commonly used operating systems including UNIX Windows, and Linux.
if we want to use LPR them the client software must be installed on a system. when a file is sent to print, it is channeled over the network by LPR network protocols to a print server or printer. That server or printer runs a print sever program, normally the Line Printer Daemon, which accepts the LPR information and adds that job to the print queue. LPR operates at the application layer of the OSI model.
Address Resolution Protocol/Reverse Address Resolution Protocol (ARP/RARP)
ARP:-network protocols works in the network layer. The basic function of the ARP network protocols is to resolve IP addresses to Media Access Control (MAC) addresses. A table, usuall called the ARP cache, is used to maintain a correlation between each MAC address. ARP provides the Protocol the protocol rules for making this correlation and providing address conversion in both directions.
if there is not an entry for the host in the ARP cache, IP sends a broadcast on the local network, asking the host the target IP address to send back it is Mac address. The communication is sent as a broadcast because without the target system’s MAC address, the source system is unable to communicate directly with the target system.
RARP:- The Reverse address Resolution Protocol performs the same function as ARP, but in reverse.In other to learn their own IP addresses to IP addresses. RARP makes it possible for applications or systems to learn their own IP address from a router or DNS server, Such a resolution comes in handy for tasks such as performing reverse lookups in DNS.
Network Time Protocol (NTP)
NTP network protocols uses the TCP transport protocol and is the protocol that facilitates the communication of time information between systems. IT is used to synchronize time of PC on a network or on the Internet. Youcan manage time synchronization by placing a command in a logon script to synchronize the time on the client with the timeserver. Use the following command: NET TIME \\computername /SET
Network News Transport Protocol (NNTP)
NNTP is an Application layer protocal that uses TCP as it is transport mechanism. it is the protocol associated with posting and retrieving messages from newsgroups. A newsgroup is the name given to a discussion forum that is hosted on a remote system. By using NNTP client software, similar to that included with many common email clients, users can post, reply, and retrieve messages. NNTP uses por 113 for communication.
Lightweight Directory Access Protocol (LSAP)
The Lightweight Directory access Protocol (LDAP) is a network protocols that provides a mechanism to access and query directory services systems. In the contest of the Network exam, these directory services systems are most likely to be Novell Directory Services and Microsoft’s Active Directory Although LDAP supports command line queries that are executed directly against the directory database, most LDAP interaction will be via utilities usch as an authentication program or locating a resource in the directory through a search utility. LDAP operates at the application layer of the OSI mode.
Lagical Link control (LLC)
It is the upper sublayer of datalink layer. The LLC later is responsible for the error and flow-control mechanisms of thr data-link layer. The LLC layer is specified in the 802.2 standard. An LLC header tells the Data Link layer what to do with a packet once a frame is received. A host will receive a frame and look in the LLC header to find out where the packet is destined for the LLc can also provide flow control and scquencing of control bits.
Media Access Control (MAC)
The first sublayer of the data-link layer is called Media Access Control (MAC). Its IEEE Specification is 802.3. The defines how packets are placed on the media. Physical addressing is defined here, as well as logical topologies.. Logical topology is the signal path through a physical topology. Line disciplins, error notification (not connection), ordered delivery of frames, and optional flow control can also be used at this sub layer. The MAC sub layer manages and controls and controls access to the network media for the protocols trying to use it. The MAC address is defined at this layer. These Physical addresses areburned into the network cards and constitute the low-level address used to determine the source and destination of network traffic.
IPX/SPX (Internrtwork Packet Exchange/ Sequence Packet Exchange/Sequence Packet Exchange)
IPXSpx is not a protocol but a protocol suite. That means it contains a lot of protocols. This protocol sute was create by Novell for use on networks. Ipx is a connectionless Layer 3 network protocol. It’s counterpart, SPX, operates at Layer 4. Although multiple Novell protocols also operate at Layer 4 ,SPX is the most commonly implemented, SPX, a reliable, connection-oriented protocols, was derived from the XNS (Xerox Network system) protocol s of the 1970s.
IPX Addressing
As IPX use the addressing scheme that is a bit different from IP. As example of as IPX address is 099A33CE:0004BA7C06EC. The 099A33CE portion represents the IPX address for the network, which is also sometimes referred to as the network number. The part 0004BA7C06EC is the MAC address of the node ,which is used for the second part of the address. The node Mac address is derived directly from the MAC address burned on to each network card, but in ipx addressing, it is expressed without the colons(:). Moreover , IPX addresses can also be written with each group of four hexadecimal characters separated by colons for example, 0000:0007:004B:7F53:04CF. In some cases, any leasing on the network address portion are dropped. For example, 00000007 can be expressed simply as 7, the address would then be 7:004B:7F53:04CF.
NetBEUI (Network Basic Input / Output system extended User Interface)
IBM developed Network Basic Input / Output system extended User interface ( NetBEUI ) But Microsoft adopted this transport protocol for use in earlier version of windows and DOS.
It is a simple network protocol and as such does not map to many layers of the OSI model. Specification, the NetBEUT protocal operates only at the transport and network layers of the OSI model. Because NETBEUI operates at only two layers, other protocols are needed to help in the network communication process. NetBEUI require NETBIOS, which map to the session layer of the OSI model, to establish a connection between two network devices; it need a redirector to alow client systems to see network resources; and it need the server massage block protocol, which map to the presentation layer of the OSI model, to provide communication between client redirectors and network services.
NetBEUI commonly was found in smaller networks due to the fact that it a non-routable protocal. because of it’s limitation NetBEUI is rarely ever used or seen today. NetBIOS is an API ( Applicationprotocol program interface ) that augment the MS-DOS (Microsoft Disk Operating System ) BIOS by adding special Functions for LANs. Almost all Windows-based LANs for PCs are based on and used NetBIOS.
AppleTalk / AppleTalk over IP (Internet Protocol)
AppleTalk is plug-and-play protocol developed by Apple computer for use on Macintosh computers. AppleTalk was designed to allpw sharing of resources such as files and printers among multiple users. any device attached to an AppleTalk network is known as a node. shows how the AppleTalk Protocol Stack maps against the OSI reference model. Learn More….
| OSL Model | AppleTalk Suite |
| Application | AFP |
| Presentation | |
| Session | AEP, ATP, NBP, RTMP, AURF |
| Transport | AARP, DDP |
| Network | Ethernet, Token Ring |
| Data Link | ASP, ADSP, ZIP, PAP |
| Physical | EtherTalk, TokenTalk |
AppleTalk supports four media-access protocals:
- EtherTalk AppleTalk over Ethernet
- LocalTalk AppleTalk over phone wire
- TokenTalk AppleTalk over Token Ring
- FDDITalk appleTalk over Fiber Distributed Data Interface (FDDI)
At the Network Layer of AppleTalk are two protocol: AppleTalk address Resolution protocol (AARP) and Datagram delivery Protocal (DDP). AARP can be compared to ARP in TCP/IP, and DDP can be compared to IP in TCP/IP DDP is Responsible for transmitting and reciving packts and provides Socket-to-socket connectivity between nodes.
Now we will discuss about five key protocol exist at AppleTalk’s Transfer Layer:
- AppleTalk Echo protocol (AEP): This network protocols is responsible for testing the possibility to reachto network nodes.
- AppleTalk transaction protocol (ATP): This network protocols is responsible for ensuring that communication btween a source and destination socket occur without any loos.
- Name Binding Protocol (NBP): This network protocols is responsible for mapping user-friendly entity names to numeric network addresses .
- Routing Table Maintenance Protocol (RTMP): This distance-vector routing protocol for AppleTalk is based on IP RIP.
- AppleTalk updatr-Based Routing Protocol (AUMP): This network protocols is an extension to RTMP that allows two noncontiguous AppleTalk networks to talk to each other by tunneling their traffic through IP using UDP ( user Datagram protocol ).
The Following four protocols of AppleTalk are of session layer:
- AppleTalk Session Protocol ( ASP): This network protocols is responsible for establishing and maintaining logical connections between clients and servers. ASP runs on top of ATP.
- AppleTalk data Stream Protocol (ADSP): This network protocols is responsible for reliable transmission of data after a session has been established between two nodes. ADSP run directly on top of DDP.
- Zone Information Protocol (ZIP): This Protocol maintains network-to-zone number mappings.
- Printer Access Protoco(PAP): This Protocol is used to establish connection between clients and servers (usually print server). PAP runs on top of ATP.
you should also mention SOI model with this contain
Right, I will try to add..
Thanks for you comments
Thanks for this article. I might also like to talk about the fact that it can end up being hard if you find yourself in school and just starting out to initiate a long credit standing. There are many individuals who are merely trying to survive and have an extended or beneficial credit history can sometimes be a difficult factor to have.